A security policy framework to help companies unlock the power of the cloud
February 2, 2015
Today’s employees have more data than ever to work with, and expect easy-to-use tools that work everywhere they do. At the same time, IT departments are tasked with deploying more services with less budget, and aren’t always able to buy or build solutions that meet every business unit’s needs and timelines. These challenges have sparked a new, hosted computing model called “the cloud.”
At LinkedIn, we quickly adopted the cloud model for our business operations data. Today we have dozens of supported applications, with more in the queue. These applications range from non-confidential services such as our business-card printing vendor to a highly confidential service we use to run our payroll systems. When evaluating a new cloud application, it’s not as simple as creating accounts and sending data, we must also ensure that the company’s data is being hosted and managed to the highest standards of security.
Organizations such as the Cloud Security Alliance have done an excellent job creating guidance around application security, but their one-size-fits-all approach does not take into account that IT security groups have to to balance security with the needs and speed of the business. To accommodate this, the Cloud Security Team at LinkedIn used guidance from the CSA, Amazon, Google, and the US National Institute of Standards and Technology (NIST) to create a framework designed to enable secure use of a wide range of applications.
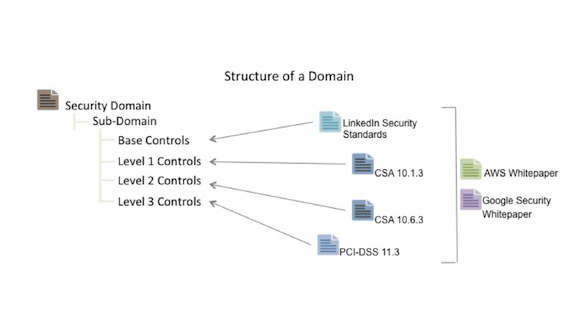
What makes this framework unique is the data modeling and leveling process, utilizing the NIST 800-60 guidance to categorize applications into one of three levels from least to most confidential. This categorization then drives a set of appropriate security controls.
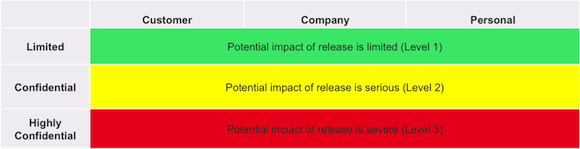
Using this strategy, we are able to apply appropriate protections, keeping corporate data safe while not acting as a roadblock to progress. The controls are primarily focused on Software-as-a-Service (SaaS) solutions, but many are applicable to Platform- or Infrastructure- as-a-Service deployments as well.
Since no two companies have the same data models and security threats, our goal is to help start a dialog where IT security professionals, as cloud consumers, can share challenges and best practices. To accomplish this, LinkedIn is releasing our policy framework under a Creative Commons Non-Commercial license. This model encourages you to cut-and-paste some or all of our framework in your organization, and contribute to the development of industry best practices.
 Download the Policy Framework (PDF)
Download the Policy Framework (PDF)
Please post your thoughts and changes. I, and the rest of the LinkedIn Cloud Security Team, look forward to your feedback!